Since its introduction in 2012, an OS X feature known as Gatekeeper has gone a long way to protecting the Macs of security novices and experts alike. Not only does it help neutralize social engineering attacks that trick less experienced users into installing trojans, code-signing requirements ensure even seasoned users that an installer app hasn't been maliciously modified as it was downloaded over an unencrypted connection.
Now, a security researcher has found a drop-dead simple technique that completely bypasses Gatekeeper, even when the protection is set to its strictest setting. The hack uses a binary file already trusted by Apple to pass through Gatekeeper. Once the Apple-trusted file is on the other side, it executes one or more malicious files that are included in the same folder. The bundled files can install a variety of nefarious programs, including password loggers, apps that capture audio and video, and botnet software.
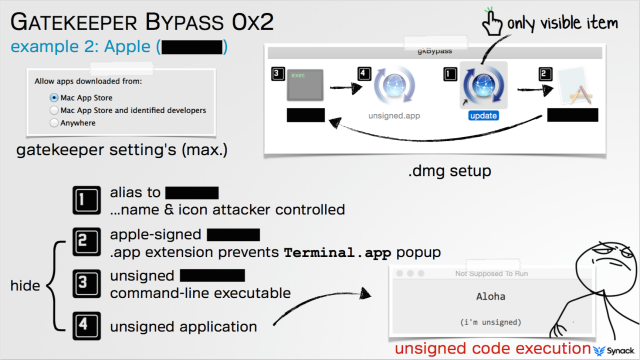
Patrick Wardle, director of research of security firm Synack, said the bypass stems from a key shortcoming in the design of Gatekeeper rather than a defect in the way it operates. Gatekeeper's sole function is to check the digital certificate of a downloaded app before it's installed to see if it's signed by an Apple-recognized developer or originated from the official Apple App Store. It was never set up to prevent apps already trusted by OS X from running in unintended or malicious ways, as the proof-of-concept exploit he developed does.
"If the application is valid—so it was signed by a developer ID or was (downloaded) from the Mac App Store—Gatekeeper basically says 'OK, I'm going to let this run,' and then Gatekeeper essentially exits," Wardle told Ars. "It doesn't monitor what that application is doing. If that application turns around and either loads or executes other content from the same directory... Gatekeeper does not examine those files."
Putting it into practice
Wardle has found a widely available binary that's already signed by Apple. Once executed, the file runs a separate app located in the same folder as the first one. At the request of Apple officials, he and Ars have agreed to withhold the names of the two files, and instead will refer to them only as Binary A and Binary B. His exploit works by renaming Binary A but otherwise making no other changes to it. He then packages it inside an Apple disk image. Because the renamed Binary A is a known file signed by Apple, it will immediately be approved by Gatekeeper and be executed by OS X.
From there, Binary A will look for Binary B located in the same folder, which in this case is the downloaded disk image. Since Gatekeeper checks only the original file an end user clicks on, Wardle's exploit swaps out the legitimate Binary B with a malicious one and bundles it in the same disk image under the same file name. Binary B needs no digital certificate to run, so it can install anything the attacker wants.
Wardle said there are similar ways to bypass Gatekeeper. One alternate method involves renaming an installer for an app such as Photoshop and bundling it with booby-trapped plugins that the app automatically opens. Because Gatekeeper will only check the first installer app, it won't warn users of the malicious plugins. Such an attack lacks practicality, however, since most end users would suspect something is amiss if the file they just downloaded installed Photoshop.
The Gatekeeper bypass could conceivably be exploited both by opportunistic criminals pushing banking trojans or similar crimeware lookalikes or state-sponsored hackers who inject malicious code into unencrypted downloads. Once an Apple-signed binary is discovered, it would require only a handful of extra lines of code to fold the bypass into an existing exploit. From then on, the exploit would be completely free of Gatekeeper intervention. Wardle said he suspects there are other Apple-trusted binaries besides the one he discovered that will also allow attackers to bypass Gatekeeper.
Help on the way
The researcher said he privately alerted Apple officials to his discovery more than 60 days ago and believes they are working on a way to fix the underlying cause or at least lessen the damage it can do to end users. An Apple spokesman confirmed that company developers are working on a patch. Wardle plans to present his findings on Thursday at the Virus Bulletin Conference in Prague, Czech Republic.
"If I can find it, you have to assume groups of hackers or more sophisticated nation states have found similar weaknesses," he said. "I'm sure there are other Apple-signed apps out there" that can also be abused to bypass Gatekeeper.
reader comments
104