Critics are calling for the ouster of Trustwave as a trusted issuer of secure sockets layer certificates after it admitted minting a credential it knew would be used by a customer to impersonate websites it didn't own.
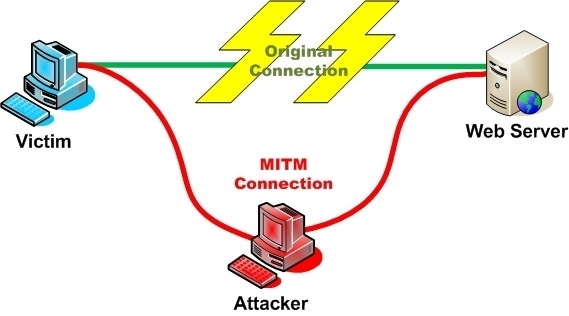
The so-called subordinate root certificate allowed the customer to issue SSL credentials that Internet Explorer and other major browsers would accept as valid for any server on the Internet. The unnamed buyer of this skeleton key used it to perform what amounted to man-in-the-middle attacks that monitored users of its internal network as they accessed SSL-encrypted websites and services. The data-loss-prevention system used a hardware security module to ensure the private key at the heart of the root certificate wasn't accidentally leaked or retrieved by hackers.
The measures haven't assuaged security experts and critics, who are calling on Mozilla to remove the Trustwave root from Firefox and Thunderbird. They argue the Mozilla CA Certificate Policy, and possibly similar requirements from other software makers, make it a violation for authorities to "knowingly issue certificates without the knowledge of the entities whose information is referenced in the certificates."
Trustwave's insistence that the subordinate certificate was used only on the customer's internal network is irrelevant, they say.
"While that interception may have been performed for a legitimate purpose, and the employees of the IT enterprise engaging in this activity may have been told about it by their employer, it doesn't change the fact that Trustwave's cert was used to impersonate sites," one of the critics, Christopher Soghoian, wrote in an e-mail to Ars. "This is a big no no, and violates Mozilla's CA rules."
Soghoian is among the members of the online discussion who are calling on Mozilla to revoke its trust in the Trustwave root. The controversy was sparked after Trustwave recently admitted to issuing the certificate, and promised to revoke it and abandon the practice in light of a recent rash of attacks on certificate authorities. It was the first known instance of an authority admitting to issuing such a key, although critics maintain the practice is common.
In a statement, Firefox director of engineering Johnathan Nightingale said Mozilla managers have yet to decide whether to banish Trustwave.
"In the interim, we are pleased to hear that this subordinate certificate is being revoked," he added. "We encourage any other CAs with similar certificates to follow Trustwave's example of disclosure and revocation."
A Microsoft spokeswoman declined to say if Trustwave's issuance of a subordinate certificate violates terms governing root authorities that are trusted in Windows.
In Trustwave's Saturday blog post, and in comments added on Tuesday to the heated discussion in the Mozilla developer forum, Trustwave representatives stressed that the holder of the subordinate root was subject to strict terms that were enforced by on-site audits. The terms required the company to disclose the practice to all users of the network, and the private keys for the cloned certificates were never available to system administrators or any other user. Trustwave has said it has issued only one such certificate, ever.
Trustwave, which calls itself "one of the most trusted brands on the internet," made the admission six months after the discovery that hackers used the root certificate belonging to Netherlands-based authority DigiNotar to mint fraudulent credentials for Google Mail, Mozilla's add-ons service, and other sensitive sites. Last year, competing authorities StartSSL and GlobalSign reported security breaches, but have said they were disrupted before attackers could forge counterfeit credentials. At least two other authorities have reported being attacked, according to a recent audit by the Electronic Frontier Foundation.
Over the past year, security experts have proposed a variety of alternatives to the complex web of trust now used to manage the net's ailing SSL system. Among them is the Convergence project devised by researcher Moxie Marlinspike. The system, which would have flagged counterfeit certificates used to snoop on some 300,000 Gmail users, has already won the qualified endorsement of security firm Qualys. Google, meanwhile, has said it has no plans to implement Convergence in its Chrome browser.
Google researchers have suggested changes of their own (PDF) designed to prevent authorities from issuing certificates without the permission of the underlying domain name holder. The proposal, which has had a chilly reception from some authorities, is intended to curb one of SSL's key weaknesses: With more than 600 bodies authorized to issue valid digital certificates trusted by major browsers, there are too many single points of failure.
Listing image by Photograph by Adam Rifkin
reader comments
69