Less than 10 percent of the most popular websites offering Secure Socket Layer protection are hardened against known attacks that could allow hackers to decrypt or tamper with encrypted traffic, researchers said Thursday.
The grim figure was generated by SSL Pulse, a website that monitors the effectiveness of the 200,000 most popular websites that use SSL, also known as Transport Layer Security, to protect e-mail and other sensitive data from being snooped on while in transit. The product of a group of SSL experts from Google, Twitter, PayPal, Qualys and other firms, SSL Pulse systematically scans all subdomains of the top-ranked sites as measured by Alexa for pages that use the protocol to prevent man-in-the-middle eavesdropping. By examining the top 200,000 SSL-enabled sites, the researchers aim to give a snapshot of the overall health of SSL protection, which is offered by an estimated 1.5 million sites in total.
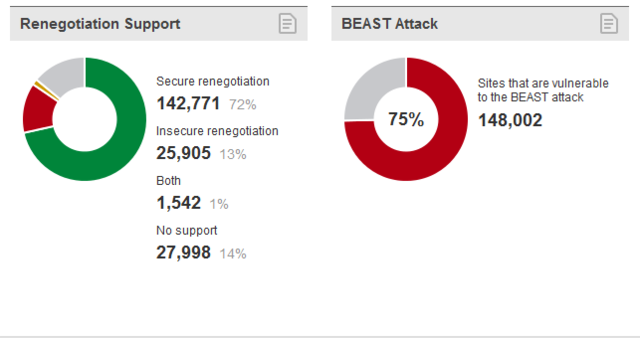
Out of the 200,000 sites examined, only 19,024 were configured to withstand an attack discovered in 2009 that allows attackers to inject data into encrypted traffic passing between two endpoints. The vulnerability resides in the SSL protocol itself and can be exploited by renegotiating the protected session, something that often happens to generate a new cryptographic key. Just a few weeks after the bug was discovered, a Turkish grad student showed how it allowed him to steal Twitter login credentials that passed through encrypted data streams.
Although the Internet Engineering Task Force signed off on a fix in early 2010 and major SSL packages have been updated to include it, only 72 percent of the sites examined by SSL Pulse were found to be safe from renegotiation exploits. Of the remainder, 13 percent were classified as "insecure renegotiation," one percent was classified as offering both secure and insecure renegotiation, and 14 percent offered no renegotiation at all.
"On the application layer, you can make mistakes and programming mistakes that completely subvert SSL," Qualys Director of Engineering Ivan Ristic told Ars.

 Loading comments...
Loading comments...
