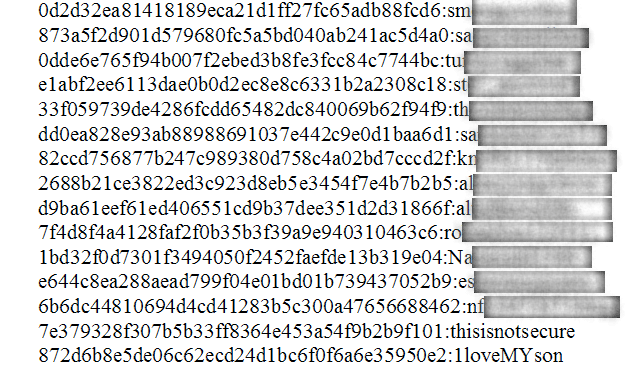
An unknown hacker has posted more than 8 million cryptographic hashes to the Internet that appear to belong to users of LinkedIn and a separate, popular dating website.
The massive dumps over the past three days came in postings to user forums dedicated to password cracking at insidepro.com. The bigger of the two lists contains almost 6.46 million passwords that have been converted into hashes using the SHA-1 cryptographic function. They use no cryptographic "salt," making the job of cracking them considerably faster. Rick Redman, a security consultant who specializes in password cracking, said the list almost certainly belongs to LinkedIn because he found a password in it that was unique to the professional social networking site. Robert Graham, CEO of Errata Security said much the same thing, as did researchers from Sophos. Several Twitter users reported similar findings.
"My [LinkedIn] password was in it and mine was 20 plus characters and was random," Redman, who works for consultancy Kore Logic Security, told Ars. With LinkedIn counting more than 160 million registered users, the list is probably a small subset, most likely because the person who obtained it cracked the weakest ones and posted only those he needed help with.
"It's pretty obvious that whoever the bad guy was cracked the easy ones and then posted these, saying, 'These are the ones I can't crack,'" Redman said. He estimates that he has cracked about 55 percent of the hashes over the past 24 hours. "I think the person has more. It's just that these are the ones they couldn't seem to get."
Update 2:01 pm PDT: In a blog post posted after this article was published, a LinkedIn official confirmed that "some of the passwords that were compromised correspond to LinkedIn accounts" and said an investigation is continuing. The company has begun notifying users known to be affected and has also implemented enhanced security measures that include hashing and salting current password databases.
The smaller of the two lists contains about 1.5 million unsalted MD5 hashes. Based on the plaintext passwords that have been cracked so far, they appear to belong to users of a popular dating website, possibly eHarmony. A statistically significant percentage of users regularly pick passcodes that identify the site hosting their account. At least 420 of the passwords in the smaller list contain the strings "eharmony" or "harmony."
The lists of hashes that Ars has seen don't include the corresponding login names, making it impossible for people to use them to gain unauthorized access to a particular user's account. But it's safe to assume that information is available to the hackers who obtained the list, and it wouldn't be a surprise if it was also available in underground forums. Ars readers should change their passwords for those two sites immediately. If they used the same password on a separate site, it should be changed there, too.
eHarmony officials didn't immediately respond to a request for comment.
The InsidePro postings provide a glimpse into the sport of collective password cracking, a forum where people gather to pool their expertise and sometimes vast amounts of computing resources.
"Please help to uncrack [these] hashes," someone with the username dwdm wrote in a June 3 post that contained the 1.5 million hashes. "All passwords are UPPERCASE."
Less than two and a half hours later, someone with the username zyx4cba posted a list that included almost 1.2 million of them, or more than 76 percent of the overall list. Two minutes later, the user LorDHash independently cracked more than 1.22 million of them and reported that about 1.2 million of the passwords were unique. As of Tuesday, following the contributions of several other users, just 98,013 uncracked hashes remained.
While forum members were busy cracking that list, dwdm on Tuesday morning posted the much larger list that Redman and others believe belongs to LinkedIn users. "Guys, need you[r] help again," dwdm wrote. Collective cracking on that list was continuing at the time of this writing Wednesday morning.
By identifying the patterns of passwords in the larger list, Redman said it's clear they were chosen by people who are accustomed to following policies enforced in larger businesses. That is, many of the passwords contained a mix of capital and lower case letters and numbers. That's another reason he suspected early on that the passwords originated on LinkedIn.
"These are business people, so a lot of them are doing it like they would in the business world," he explained. "They didn't have to use uppercase, but they are. A lot of the patterns we're seeing are the more complicated ones. I cracked a 15-character one that was just the top row of the keyboard."
Story updated to add link to Errata Security blog post, and to correct the percentage of passwords Redman has cracked.
reader comments
134