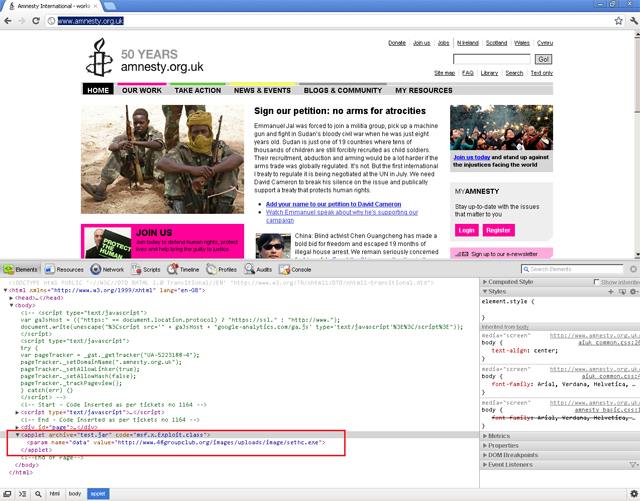
Shattering the myth that only disreputable sites push malware, Amnesty International's UK website was recently compromised and used to install a notorious backdoor trojan that allows hackers to spy on political activists and government employees, security researchers said.
People visiting Amnesty.org.uk on Wednesday and Thursday were exposed to malicious code that exploited a now-patched vulnerability in Oracle's Java software framework, according to a blog post published Friday by Websense. End users who hadn't yet applied the patch were infected with Gh0stRat, a family of malware that siphons sensitive data from victims' machines and can also operate Web cams and microphones in real time. The trojan came to light in 2009 when researchers reported that it infiltrated government and private offices in 103 countries. That included computers belonging to the Dalai Lama.
The Java vulnerability targeted on the Amnesty International site has been used in the past to install malware on computers running both Microsoft Windows and Apple's OS X. Recently, similar espionage attacks have migrated to OS X, and the Flashback malware attack believed to have infected more than 500,000 Macs targeted the same bug. Based on the Websense post, however, it appears this week's attacks infected only Windows users.
The file used to install the backdoor trojan was digitally signed by certificate authority VeriSign on behalf of a company called Tencent Technology, making the attack on Amnesty International visitors more sophisticated. The imprimatur is intended to tamp down visitors' suspicions by giving the software an air of legitimacy. Stolen or forged digital certificates have been used in other malware attacks, most notably in those that spread the Stuxnet worm that disrupted Iran's nuclear program.
The Amnesty International incident is the latest reminder that users can be infected even when they visit websites they trust and frequent often. It challenges the myth that as long as people steer clear of sites offering porn, pirated movies and software, and other unsavory content, they aren't susceptible to attacks that surreptitiously install malware on their systems.
In a world where a single unpatched vulnerability can lead to an infected system, the most important security precaution users of any platform can take is to install security updates within hours of them becoming available. The notable exception to this advice: users should install updates only on networks they control, because public networks, including those provided by hotels, may try to push fake updates that also infect end-user machines, as the FBI warned earlier this week. Users who are on the road or at an Internet cafe down the street are better off waiting until they get home to patch their systems.
reader comments
32