Marketers at security giant McAfee peddle their Secure trust mark service as an easy way for online merchants to showcase the safety of their websites. These sites include a link to a seal showing it has passed a rigorous security scan that is performed daily. But a pair of security consultants say the program in many cases can tip off malicious hackers to easy-to-exploit vulnerabilities that might otherwise not be found.
That's because a design flaw in the service, and in competing services offered by Trust Guard and others, makes it easy to discover in almost real time when a customer has had the seal revoked. A revocation is a either a sign the site has failed to pay its bill, has been inaccessible for a sustained period of time, or most crucially, is no longer able to pass the daily security test.
"It's basically McAfee, Trust Guard, and all these other guys raising the flag, saying, 'Hey guys, these sites are vulnerable to attack. Go after them,'" Shane MacDougall, a security researcher with Tactical Intelligence, told Ars. "They all suffer from this fatal design flaw, which is you're raising a flag over your castle and you're pulling the flag down when you're vulnerable to attack. Who in their right mind would do that?"
Representatives from McAfee and Trust Guard didn't respond to e-mails seeking comment for this article.
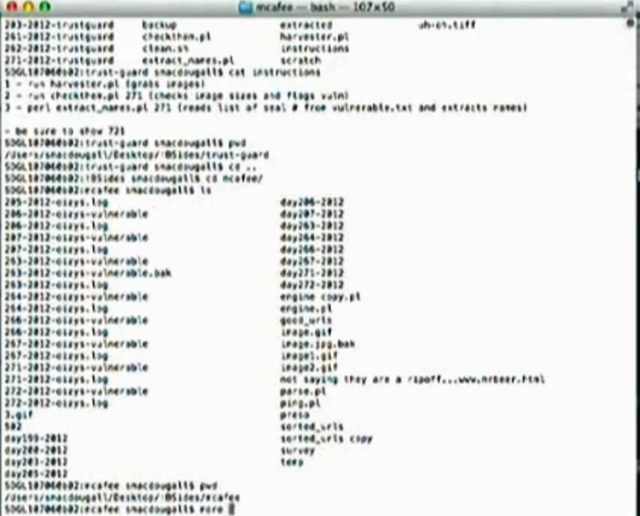
At last week's DerbyCon security conference in Louisville, Kentucky, MacDougall unveiled Oizys, a tool that automatically enumerates websites that have recently had their seals removed. Designed by MacDougall and colleague Jay James, it works by searching publicly accessible website folders that store the images for each customer that has signed up for the service. When the normal icon has been replaced by a transparent image that is 1 pixel by 1 pixel in size, the script indexes the corresponding website. In cases where the domain names have been obscured, Oizys (an allusion to the Greek goddess of misery) uses optical character recognition to pull the domain name from a corresponding business card.
It's not the first time security researchers have poked holes in the website trust mark programs, which attempt to act as a good housekeeping seal of approval for e-commerce sites. In 2008, consultant Russ McRee documented XSS, or cross-site scripting errors in five sites that prominently carried the McAfee marks, which at the time carried the words "Hacker Safe." McRee's findings came a few months after a separate group of researchers documented security bugs in 60 e-commerce sites that also carried McAfee's "Hacker Safe" seal.
A McAfee spokesman at the time said that XSS bugs were rated less severely than other types of Web vulnerabilities such as SQL injection vulnerabilities, which are the result of Web applications that take user-supplied input to complete back-end database commands. XSS flaws, by contrast, allow attackers to execute arbitrary JavaScript or HTML in an end-user's browser in the context of the website they are visiting.
The effectiveness of the technique MacDougall and James devised is that it allows hackers to identify sites that are likely to succumb to attack without directly scanning them. Attackers are then free to probe the list using programs such as Nessus. MacDougall said he identified other weaknesses in various trust mark programs, including a delay of three days to one week from the time a site fails a security scan and when its seal is removed.
Listing image by Most uncool
reader comments
23