WebSocketサーバを使ってみよう! Jul 2011
- 1. WebSocket July 2011 1
- 2. http://j.mp/ws201107 2
- 4. 4
- 5. WebSocket 5
- 6. WebSocket 6
- 7. HTML5 • • • CSS3 • • • • 3D • 7
- 8. WebSocket • • 8
- 10. shirasu.ws • https://github.com/michilu/shirasu • Misultin HTTP • Erlang 10
- 11. shirasu.ws • Fedora Linux RPM Red Hat Enterprise Linux • YAML • 11
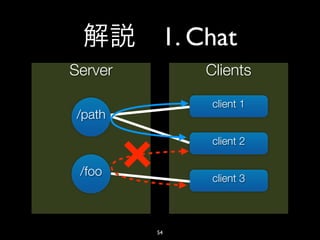
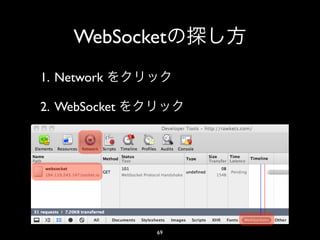
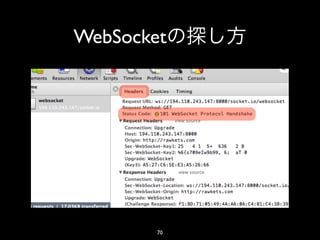
- 12. shirasu.ws • path path • HTTP HTTP • HTTP GET HTTP WebSocket 12
- 13. 13
- 14. • Fedora 14 Amazon EC2 • Shirasu WebSocket 14
- 15. Amazon EC2 • AWS • AWS • Fedora 14 • ssh 15
- 16. AWS • AWS http://j.mp/r3KAwO 16
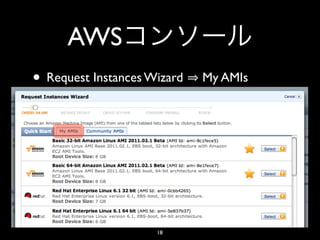
- 17. AWS • EC2 US East EC2 Dashboard Launch Instance 17
- 18. AWS • Request Instances Wizard My AMIs 18
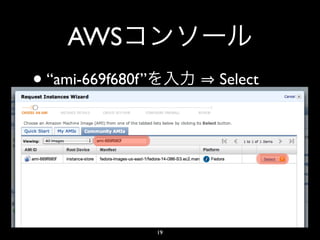
- 19. AWS • “ami-669f680f” Select 19
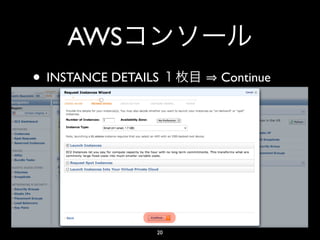
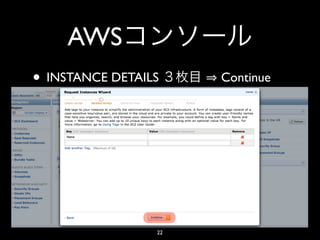
- 20. AWS • INSTANCE DETAILS Continue 20
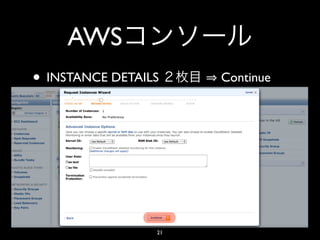
- 21. AWS • INSTANCE DETAILS Continue 21
- 22. AWS • INSTANCE DETAILS Continue 22
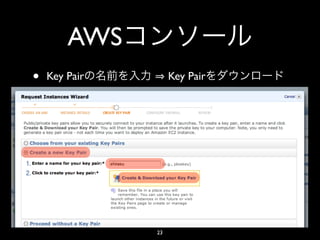
- 23. AWS • Key Pair Key Pair 23
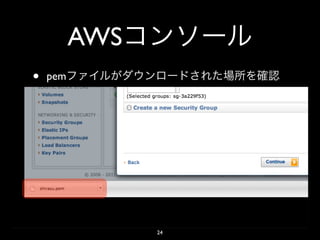
- 24. AWS • pem 24
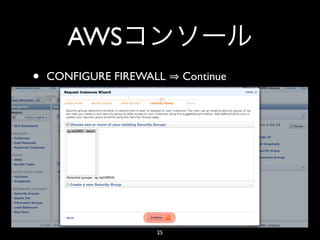
- 25. AWS • CONFIGURE FIREWALL Continue 25
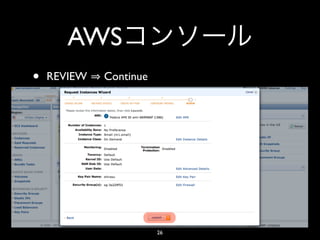
- 26. AWS • REVIEW Continue 26
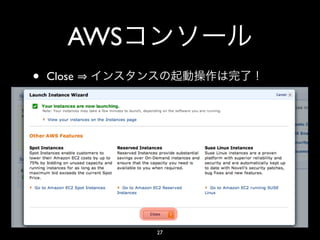
- 27. AWS • Close 27
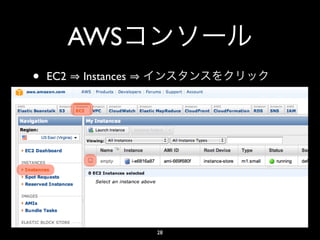
- 28. AWS • EC2 Instances 28
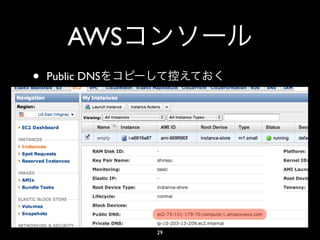
- 29. AWS • Public DNS 29
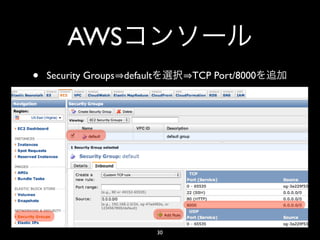
- 30. AWS • Security Groups default TCP Port/8000 30
- 31. • 31
- 32. • pem $ chmod 600 ~/Downloads/shirasu.pem 32
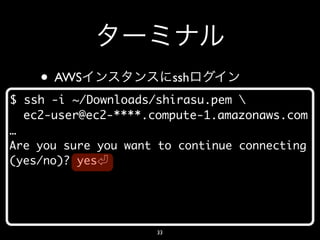
- 33. • AWS ssh $ ssh -i ~/Downloads/shirasu.pem ec2-user@ec2-****.compute-1.amazonaws.com … Are you sure you want to continue connecting (yes/no)? yes 33
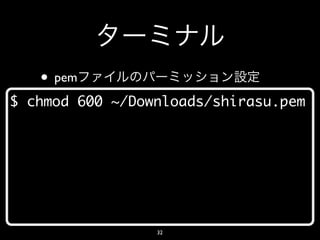
- 34. • AWS ssh … Appliance: fedora-14 appliance 1.0 Hostname: ip-10-203-13-209 IP Address: 10.203.13.209 [ec2-user@ip-10-203-13-209 ~]$ 34
- 35. Amazon EC2 • shirasu RPM • • shirasu 35
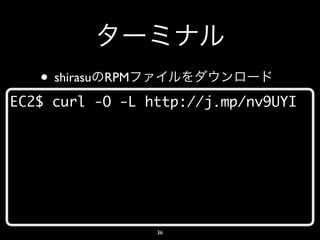
- 36. • shirasu RPM EC2$ curl -O -L http://j.mp/nv9UYI 36
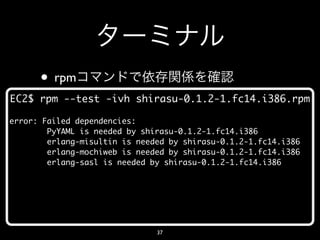
- 37. • rpm EC2$ rpm --test -ivh shirasu-0.1.2-1.fc14.i386.rpm error: Failed dependencies: PyYAML is needed by shirasu-0.1.2-1.fc14.i386 erlang-misultin is needed by shirasu-0.1.2-1.fc14.i386 erlang-mochiweb is needed by shirasu-0.1.2-1.fc14.i386 erlang-sasl is needed by shirasu-0.1.2-1.fc14.i386 37
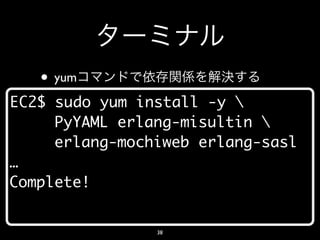
- 38. • yum EC2$ sudo yum install -y PyYAML erlang-misultin erlang-mochiweb erlang-sasl … Complete! 38
- 39. • rpm shirasu EC2$ sudo rpm -ivh shirasu-0.1.2-1.fc14.i386.rpm Preparing... ########################################### [100%] 1:shirasu ########################################### [100%] 39
- 40. Amazon EC2 • shirasu • WebSocket • shirasu • shirasu 40
- 41. • shirasu EC2$ sudo service shirasu start Starting Shirasu: [ OK ] 41
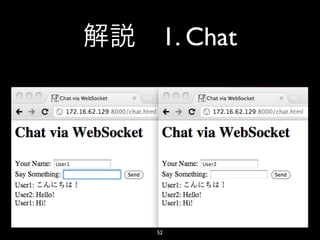
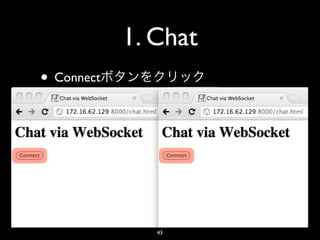
- 43. 1. Chat • Connect 43
- 44. 1. Chat • Send 44
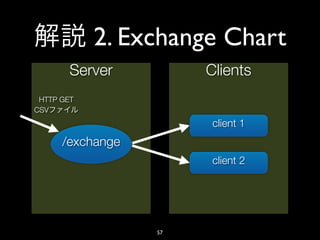
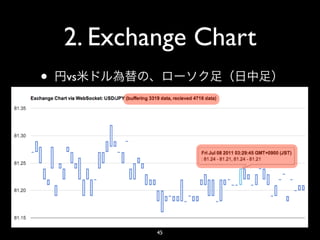
- 45. 2. Exchange Chart • vs 45
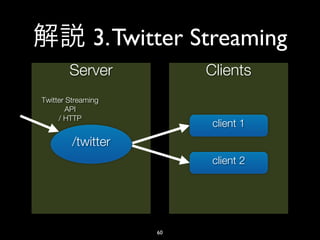
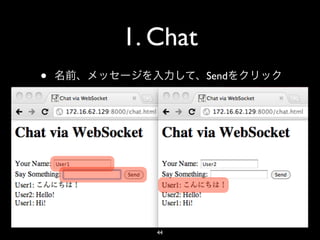
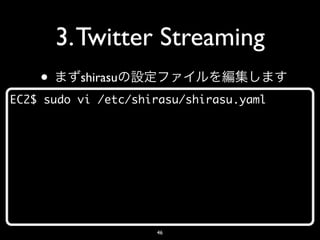
- 46. 3. Twitter Streaming • shirasu EC2$ sudo vi /etc/shirasu/shirasu.yaml 46
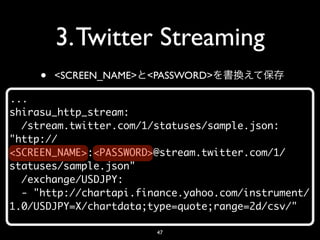
- 47. 3. Twitter Streaming • <SCREEN_NAME> <PASSWORD> ... shirasu_http_stream: /stream.twitter.com/1/statuses/sample.json: "http:// <SCREEN_NAME>:<PASSWORD>@stream.twitter.com/1/ statuses/sample.json" /exchange/USDJPY: - "http://chartapi.finance.yahoo.com/instrument/ 1.0/USDJPY=X/chartdata;type=quote;range=2d/csv/" 47
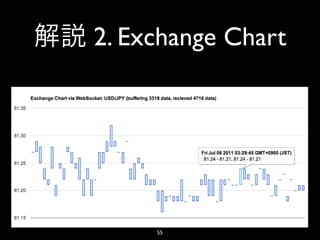
- 48. 3. Twitter Streaming • shirasu EC2$ sudo service shirasu reload Reloading Shirasu: [ OK ] 48
- 49. 3. Twitter Streaming • Twitter Streaming API WebSocket 49
- 50. • shirasu EC2$ sudo service shirasu stop Stopping Shirasu: [ OK ] 50
- 51. 51
- 52. 1. Chat 52
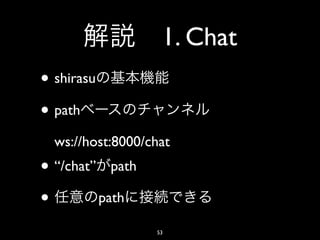
- 53. 1. Chat • shirasu • path ws://host:8000/chat • “/chat” path • path 53
- 54. 1. Chat Server Clients client 1 /path client 2 /foo client 3 54
- 55. 2. Exchange Chart 55
- 56. 2. Exchange Chart • HTTP GET • HTTP CSV WebSocket • http://chartapi.finance.yahoo.com/ chartapi.finance.yahoo.cominstrument/1.0/ USDJPY=X/ chartdata;type=quote;range=2d/csv/ 56
- 57. 2. Exchange Chart Server Clients HTTP GET CSV client 1 /exchange client 2 57
- 58. 3. Twitter Streaming 58
- 59. 3. Twitter Streaming • HTTP GET • HTTP HTTP WebSocket • http:// <SCREEN_NAME>:<PASSWORD>@ stream.twitter.com/1/statuses/sample.json 59
- 60. 3. Twitter Streaming Server Clients Twitter Streaming API / HTTP client 1 /twitter client 2 60
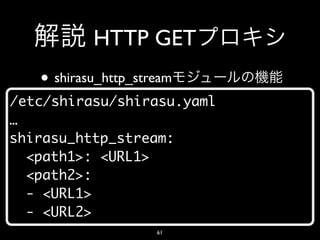
- 61. HTTP GET • shirasu_http_stream /etc/shirasu/shirasu.yaml … shirasu_http_stream: <path1>: <URL1> <path2>: - <URL1> - <URL2> 61
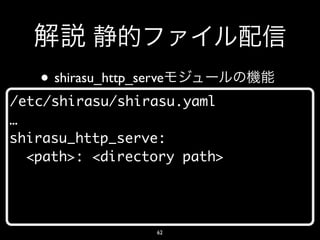
- 62. • shirasu_http_serve /etc/shirasu/shirasu.yaml … shirasu_http_serve: <path>: <directory path> 62
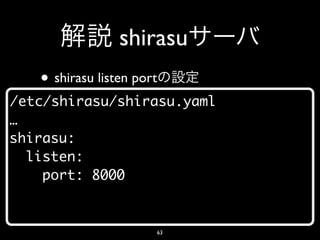
- 63. shirasu • shirasu listen port /etc/shirasu/shirasu.yaml … shirasu: listen: port: 8000 63
- 64. Amazon EC2 • AWS • 64
- 65. AWS • AWS http://j.mp/r3KAwO 65
- 66. AWS • EC2 Instance Instance Action Terminate 66
- 67. WebSocket 67
- 70. WebSocket 70
- 71. • WebSocket EC2 • • shirasu • shirasu 71
- 73. http://j.mp/o5jxmI 73
Editor's Notes
- #2: \n
- #3: \n
- #4: \n
- #5: \n
- #6: \n
- #7: \n
- #8: HTML5&#x3067;&#x306F;&#x3001;&#x30B5;&#x30A4;&#x30C8;&#x306E;&#x6A5F;&#x80FD;&#x3092;&#x8868;&#x73FE;&#x3059;&#x308B;&#x305F;&#x3081;&#x306E;&#x30D0;&#x30C3;&#x30B8;&#x304C;&#x914D;&#x5E03;&#x3055;&#x308C;&#x3066;&#x3044;&#x307E;&#x3059;&#x3002;&#x63A5;&#x7D9A;&#x6027;&#x3001;CSS3&#x3001;&#x30C7;&#x30D0;&#x30A4;&#x30B9;&#x30A2;&#x30AF;&#x30BB;&#x30B9;&#x3001;3D&#x30B0;&#x30E9;&#x30D5;&#x30A3;&#x30C3;&#x30AF;&#x30B9;&#x3001;&#x30A8;&#x30D5;&#x30A7;&#x30AF;&#x30C8;&#x3001;&#x30DE;&#x30EB;&#x30C1;&#x30E1;&#x30C7;&#x30A3;&#x30A2;&#x3001;&#x30D1;&#x30D5;&#x30A9;&#x30FC;&#x30DE;&#x30F3;&#x30B9;&#x3001;&#x7D71;&#x5408;&#x3001;&#x610F;&#x5473;&#x8AD6;&#x3001;&#x30AA;&#x30D5;&#x30E9;&#x30A4;&#x30F3;&#x3001;&#x30B9;&#x30C8;&#x30EC;&#x30FC;&#x30B8;&#x3002;WebSocket&#x3092;&#x3053;&#x308C;&#x3089;&#x306B;&#x306A;&#x305E;&#x3089;&#x3048;&#x308B;&#x3068;&#x3001;&#x6B21;&#x306E;&#x3088;&#x3046;&#x306B;&#x306A;&#x308A;&#x307E;&#x3059;&#x3002;\n
- #9: &#x63A5;&#x7D9A;&#x6027;&#x306E;&#x63D0;&#x4F9B;&#x3001;&#x30D1;&#x30D5;&#x30A9;&#x30FC;&#x30DE;&#x30F3;&#x30B9;&#x3001;&#x7D71;&#x5408;&#x306B;&#x5BC4;&#x4E0E;&#x3059;&#x308B;&#x3001;&#x3068;&#x3044;&#x3048;&#x307E;&#x3059;&#x3002;\n
- #10: \n
- #11: \n
- #12: \n
- #13: \n
- #14: &#x3067;&#x306F;&#x3001;&#x3053;&#x308C;&#x3089;&#x306E;&#x6A5F;&#x80FD;&#x306B;&#x5B9F;&#x969B;&#x306B;&#x89E6;&#x308C;&#x3066;&#x307F;&#x307E;&#x3057;&#x3087;&#x3046;\n
- #15: \n
- #16: \n
- #17: \n
- #18: \n
- #19: \n
- #20: \n
- #21: \n
- #22: \n
- #23: \n
- #24: \n
- #25: \n
- #26: \n
- #27: \n
- #28: \n
- #29: \n
- #30: \n
- #31: \n
- #32: \n
- #33: \n
- #34: \n
- #35: \n
- #36: \n
- #37: \n
- #38: \n
- #39: \n
- #40: \n
- #41: \n
- #42: \n
- #43: \n
- #44: \n
- #45: \n
- #46: \n
- #47: \n
- #48: \n
- #49: \n
- #50: \n
- #51: \n
- #52: &#x3067;&#x306F;&#x3001;&#x30C7;&#x30E2;&#x3067;&#x4F7F;&#x3063;&#x305F;&#x6A5F;&#x80FD;&#x306B;&#x3064;&#x3044;&#x3066;&#x89E3;&#x8AAC;&#x3057;&#x3066;&#x3044;&#x304D;&#x307E;&#x3059;\n
- #53: \n
- #54: \n
- #55: \n
- #56: \n
- #57: \n
- #58: \n
- #59: \n
- #60: \n
- #61: \n
- #62: \n
- #63: \n
- #64: \n
- #65: \n
- #66: \n
- #67: \n
- #68: WebSocket&#x306F;&#x76EE;&#x7ACB;&#x305F;&#x306A;&#x3044;&#x5B58;&#x5728;&#x3067;&#x3059;&#x3002;&#x88CF;&#x65B9;&#x3057;&#x3054;&#x3068;&#x3068;&#x3044;&#x3063;&#x305F;&#x3068;&#x3053;&#x308D;&#x3067;&#x3057;&#x3087;&#x3046;&#x304B;&#x3002;&#x3054;&#x5B58;&#x77E5;&#x306E;&#x65B9;&#x3082;&#x3044;&#x3089;&#x3063;&#x3057;&#x3083;&#x308B;&#x3068;&#x601D;&#x3044;&#x307E;&#x3059;&#x304C;&#x3001;WebSocket&#x306E;&#x63A2;&#x3057;&#x65B9;&#x3092;&#x8AAC;&#x660E;&#x3057;&#x305F;&#x3044;&#x3068;&#x601D;&#x3044;&#x307E;&#x3059;&#x3002;\n
- #69: Google&#x306E;&#x30D6;&#x30E9;&#x30A6;&#x30B6;&#x3001;&#x30AF;&#x30ED;&#x30FC;&#x30E0;&#x3082;&#x5834;&#x5408;&#x3067;&#x3059;&#x3002;\n
- #70: \n
- #71: \n
- #72: \n
- #73: \n
- #74: \n














![• AWS ssh
…
Appliance: fedora-14 appliance 1.0
Hostname: ip-10-203-13-209
IP Address: 10.203.13.209
[ec2-user@ip-10-203-13-209 ~]$
34](https://image.slidesharecdn.com/ws201107osc-110714074354-phpapp02/85/WebSocket-Jul-2011-34-320.jpg)

![• rpm shirasu
EC2$ sudo rpm -ivh shirasu-0.1.2-1.fc14.i386.rpm
Preparing... ########################################### [100%]
1:shirasu ########################################### [100%]
39](https://image.slidesharecdn.com/ws201107osc-110714074354-phpapp02/85/WebSocket-Jul-2011-39-320.jpg)

![• shirasu
EC2$ sudo service shirasu start
Starting Shirasu: [ OK ]
41](https://image.slidesharecdn.com/ws201107osc-110714074354-phpapp02/85/WebSocket-Jul-2011-41-320.jpg)
![3. Twitter Streaming
• shirasu
EC2$ sudo service shirasu reload
Reloading Shirasu: [ OK ]
48](https://image.slidesharecdn.com/ws201107osc-110714074354-phpapp02/85/WebSocket-Jul-2011-48-320.jpg)
![• shirasu
EC2$ sudo service shirasu stop
Stopping Shirasu: [ OK ]
50](https://image.slidesharecdn.com/ws201107osc-110714074354-phpapp02/85/WebSocket-Jul-2011-50-320.jpg)